This is a revision of a previous post I did. In this version there are fewer steps that need to be performed in the policy. The key here is Item Level targeting, it allows you to apply policies to specific targets in your Active Directory. In this case the target would be a specific computer.
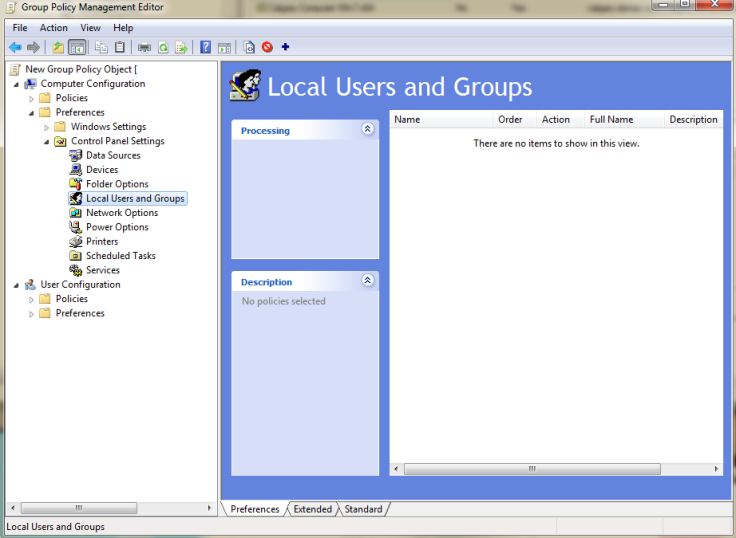
Open up your group policy managment console. Via the run command if you’re on the server, gpmc.msc. I run my policy manager from a Win 7 desktop on the domain, for this you need to install and setup the Remote Server Administration Tools, and run them with Domain Admin credentials. Once you have this open navigate down through your forest and domain to the right organizational unit (ou) where your new admin policy will sit. Generally you want to apply this in the computer OU, as the policy will be affecting desktops on your domain.
Right click on the OU and select “Create a GPO in this domain, and Link it here…“. Give the new Group Policy Object a new name and click OK. Now right click the new GPO and select “Edit…“, this will bring up the GPO editor.
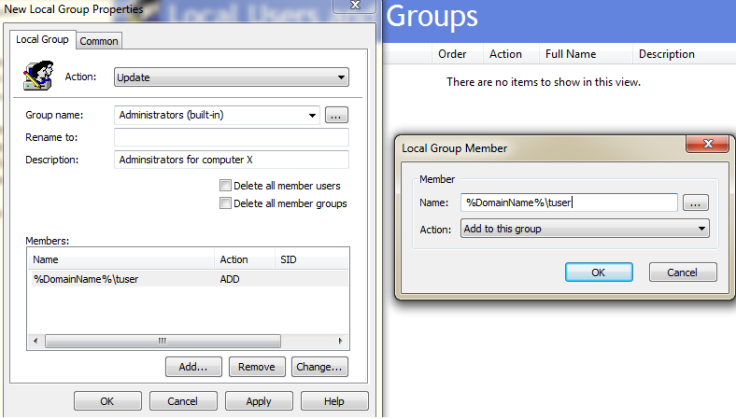
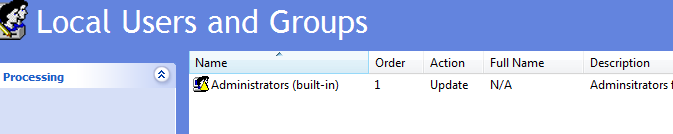
Since this policy applies to a specific computer we will select the Computer Configuration, Preferences, Control Panel Settings, and Local Users and Groups. On the right pane of this option right click and select New, Local Group. In the properties of this for Action: select Update. Group name: will be Administrators (built-in), this is the local Administrators group on all PCs. Rename to: renames the Administrators group on the target PC. Description: is just a description you might want to put in here “Administrators for computer X”. Next click Add under the Members: pane. This will bring up the Local Group Member prompt. In the Name: field type in %DomainName%\userid , where the userid is a specific logon ID and in my case tuser or my domain Test User account. %DomainName% is a variable and in this case it is the domain that the GPO resides in. If you want to see all the available variables hit F3 in the Name: field.
Click OK on the Local Group Member prompt.
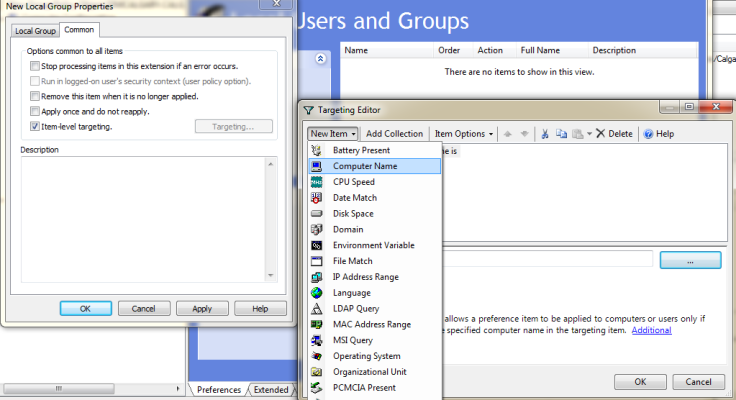
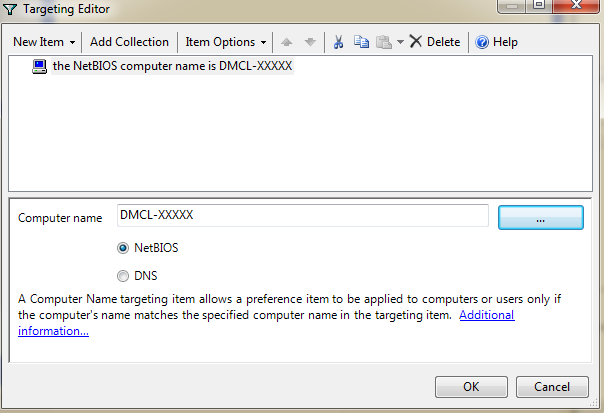
Now click the Common tab in the New Local Group Properties window. Here is where we target which computer that this policy will be applied to. On the Common tab check off Item-level targeting and click the Targeting… button.
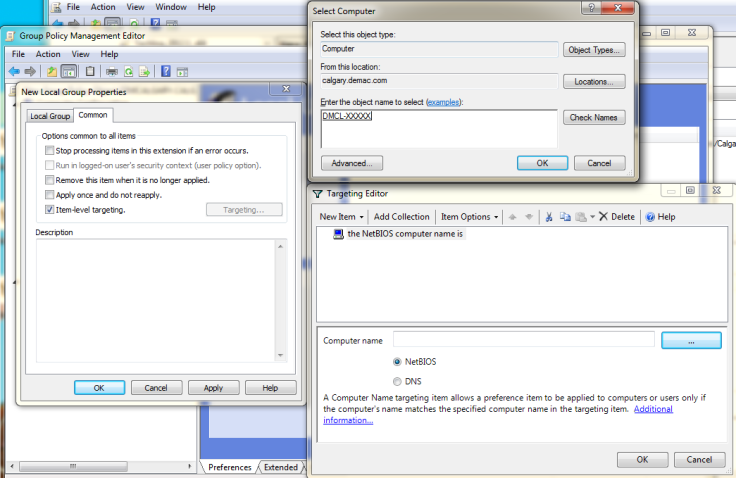
In the target editor on the top left select New Item and Computer Name. the NetBIOS computer name is should appear. In the pane below click the “…” button, here is where you select the computer this policy will apply to. Type in a computer name and click Check Names, it should underline the computer name if found correctly.
Click OK, OK, and OK. Congratulations you have successfully assigned a user to the local administrator group on a single computer on the domain.
You can also rename this to reflect more closely what the Action does. Highlight it and press F2, then rename.
Go ahead, close the Group Policy Management Editor, you’re done.
NOTE: If you want to add a single user on the network as an Administrator on all the network computers your best bet for Item Level targeting is to create a Security Group and make all Domain computers members of this group. One you’ve done that use Item Level targeting and target this said group.

Thank you, some of my users need local admin and this is perfect. Much better than doing it manually on each pc!
You’re welcome.
Hi N.D. I am trying to figure out what a friend did to his laptop. Win 8.1 OS he made a standard user account and now can now get admin right to make anything but minor changes to his computer. Most give him a pop up stating You need to enter a admin code to access but the only option to the pop up asking for admin rights is NO. The yes is not available and there is no available text box to enter any data. I see that in outlook.com many need to get admin activated but only state that it had been done and good to go. Can you direct me in the right direction to remedy this please? Thank you Bam Bam. PS his domain is available if needed but I am reluctant to give out others info willingly unless it is required where I have permission to share. Thank you for your time.
You have two options, give that standard account admin rights on said PC or you can use the run as administrator option. If you need to run something with admin rights if you hold “shift” and right click an item you get the run as administrator option. Alternatively if you right click any item and select properties, and click the Compatibility tab, you’ll see the Privilege Level check box, “Run this program as an administrator” check this off and it should prompt you for domain credentials.
If none of these options are available, then perhaps he created a “Guest” account and not a standard “User” account. Double check this setting.
Hi ND, I came across this post when I was searching for a how to for using ILT with an LDAP query. I would like to apply my policy only to servers that have a certain string in the hostname, like SQL. My LDAP query (&(objectCategory=Computer)(name=*sql*)) is running fine but still the GPO is applied to all servers in that OU. I do not want to create another OU only for these servers. I want to keep my flat OU structure as much as possible.
Any idea how it should be done correctly?
gpupdate /force didn’t solve the issue but a reboot did. Now I tried several different queries and it is working as expected.
Yes you should always reboot after doing a gpupdate as some policies are only refreshed at boot time.
Hi ND, Very interesting article.
I came across it because I am trying to figure out how to use policy to assign groups based on the servers name.
I.e. Server A will have a group called SRV_A_Admin in the local administrators group, Server B will have SRV_B_Admin and so on.
This seems problematic to do via Group Policy.
Do you have any ideas about how to do this?
It’s simple instead of adding individual users you add an AD Group.
Create a AD group called SRV_A_Admin, add the admin users to said group.
Put the users you want to be admins in there.
Now create a new Group Policy Object(GPO) and edit the policy.
User Config – Preferences – Control Panel Settings – New – Local Group
Action: Select “update”
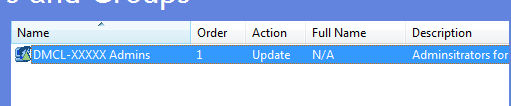
Group Name: Adminsitrators (built-in) Members: your_domain_name\SRV_A_Admin (if you click Add.. and then the 3 dot button you can locate the group in your AD)
On the common tab check off Item-level targeting. Target the server by selecting New Item and Computer name select Server A from Active Directory.
Repeat for Server B
Great post, with great details. My question is does this method also remove all unknown admins that have already been assigned, or do I need to use the previous method you posted to accomplish that as well?
No it will only Update the Administrators, a la add new ones.
I know this is an older thread but I am curious if anyone has seen this behavior: This policy works great on my Win7 machines, however it seems like on Win10 the policy isn’t restricting based on the item level targeting. So instead of a one to one relationship between a user and target machine, I am getting all users in the policy added to the admin group on win10 machines that they shouldn’t be admins on based on the item level targeting. Has anyone else come across this issue?
I am running both Windows 7 and Windows 10 machines on my domain. I have successfully setup admins via this policy on both OS versions.
What Active Directory schema version are you using?
Thank you!!!
I spent all day searching the web to find this solution. Worked perfectly.
Hello,
I want to create 2 local admin gpo , one for my system support admins which they must have local admin rights for all end user computers(not servers) and the other one is for my consultants ,they will have admin rights only in a couple server.
What should i do for that?
Thanks